In today's rapidly evolving technological landscape, businesses of all sizes are increasingly turning to Managed Service Providers (MSPs) to handle...
Read More
Blogs
Knowledge, advice and opinion on IT
How Does the FTC’s Amended Safeguards Rule Affect Your Business?
Trave Harmon
/ April 19, 2024
How Does the FTC’s Amended Safeguards Rule Affect Your Business? With cyber threats evolving and data breaches becoming more...
Read More
Understanding Co-Managed IT: A Guide to Strategic Business Partnerships
Trave Harmon
/ April 11, 2024
In today's fast-paced digital landscape, businesses of all sizes are increasingly reliant on technology to drive productivity, innovation, and growth....
Read More
Ensuring Manufacturing IT Compliance: Essential Areas to Consider
Trave Harmon
/ April 11, 2024
In today's global business environment, meeting regulatory requirements is critical for manufacturing industries. Compliance ensures that products are safe, operations...
Read More
A Guide to Conducting a Server Health Check: Ensuring Smooth Operations for Your Business
Trave Harmon
/ April 8, 2024
In today's digital landscape, where businesses rely heavily on technology infrastructure, ensuring the health and stability of servers should be...
Read More
Securing Our Water: The White House Sounds the Alarm on Cyber Threats
Trave Harmon
/ March 25, 2024
Cybersecurity Imperatives for Water Utilities: Strengthening Our Shield Amid rising concerns over the safety and resilience of the United States' critical...
Read More
$22 Million Paid to Hackers in Change Healthcare Ransomware Event
Trave Harmon
/ March 6, 2024
In a striking development, hackers behind the Change Healthcare ransomware attack have just secured a $22 million payment. This significant...
Read More
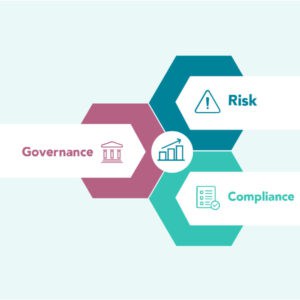
Why Governance, Risk, and Compliance Must Involve Cybersecurity
Trave Harmon
/ February 29, 2024
Understanding why governance, risk, and compliance (GRC) must involve cybersecurity is crucial for small businesses aiming to protect their assets...
Read More
Securing American Ports: A Bold Move Against Cyber Threats
Trave Harmon
/ February 28, 2024
In a decisive move to fortify America's maritime assets, the White House has issued an Executive Order aimed at enhancing...
Read More
DOJ and International Allies Take Down Lockbit: A Win for Small Businesses
Trave Harmon
/ February 20, 2024
In a significant operation, the Department of Justice, alongside international partners, has seized servers belonging to the notorious ransomware group...
Read More
Health Care Data Breaches Skyrocket in 2023: A Small Business Nightmare
Trave Harmon
/ February 19, 2024
Health care data breaches have hit an all-time high in 2023, posing unprecedented challenges for small businesses. The ripple effects...
Read More
Physical Windows Server Health Checks Guide
Trave Harmon
/ February 14, 2024
Understanding the importance of physical Windows server health checks is crucial for maintaining the integrity and performance of your IT...
Read More
New Federal Trade Commission Rules on Data Security
Trave Harmon
/ February 4, 2024
The Federal Trade Commission (FTC) has recently implemented stringent data breach notification requirements, marking a pivotal shift in data security...
Read More
Exploring the Top 3 Web Video Conferencing Services: A Comprehensive Guide
Trave Harmon
/ February 3, 2024
In our exploration of the Top 3 Web Video Conferencing Services, we delve into the digital realm where communication and...
Read More
Unleashing Productivity with Multi-Monitor Setups: Dual, Triple, and Quad Screens in Business
Trave Harmon
/ February 1, 2024
In business where maximizing productivity is crucial, multi-monitor setups, including dual, triple, and quad screens, have emerged as powerful tools...
Read More
Strengthening Cyber Defense: The Role of the Cybersecurity Information Sharing Act
Trave Harmon
/ January 31, 2024
The Cybersecurity Information Sharing Act (CISA) plays a crucial role in strengthening national defense by enhancing cyber threat intelligence sharing...
Read More
Navigating Cyber Threats: Essential Firewall Strategies for Small Businesses
Trave Harmon
/ January 30, 2024
In 2024, small businesses face an ever-evolving cyber threat landscape, making the implementation of effective firewall strategies more crucial than...
Read More
Emerging Compliance Challenges: DOJ and FTC Reinforce Business Communication Retention
Trave Harmon
/ January 29, 2024
The DOJ and FTC emphasize the need for businesses to retain communications, particularly on ephemeral messaging apps, to comply with...
Read More
Massive $15M Gamee Token Hack: A Blow to the Gaming World
Trave Harmon
/ January 26, 2024
In a stunning breach of security, the Gamee Token (GMEE) ecosystem, a cornerstone of the GAMEE gaming platform, was hit...
Read More
MGM Casino Hack: Enhanced Phishing Training, Monitoring, and Network Security Needed
Trave Harmon
/ January 25, 2024
Explore the intricacies of the MGM Casino Hack and understand the critical need for robust phishing training, vigilant monitoring, and...
Read More